Subscribe a Webhook to get WhatsApp flows results
How to configure a Rule?
- Log in to Truora’s platform.
- From the sidebar menu, select Webhooks/Automations.
- Click on the “New Rule” button to begin setting up a new webhook rule.
- Enter the name of your rule in the Rule Name field. Optionally, provide a brief description in the Description field.
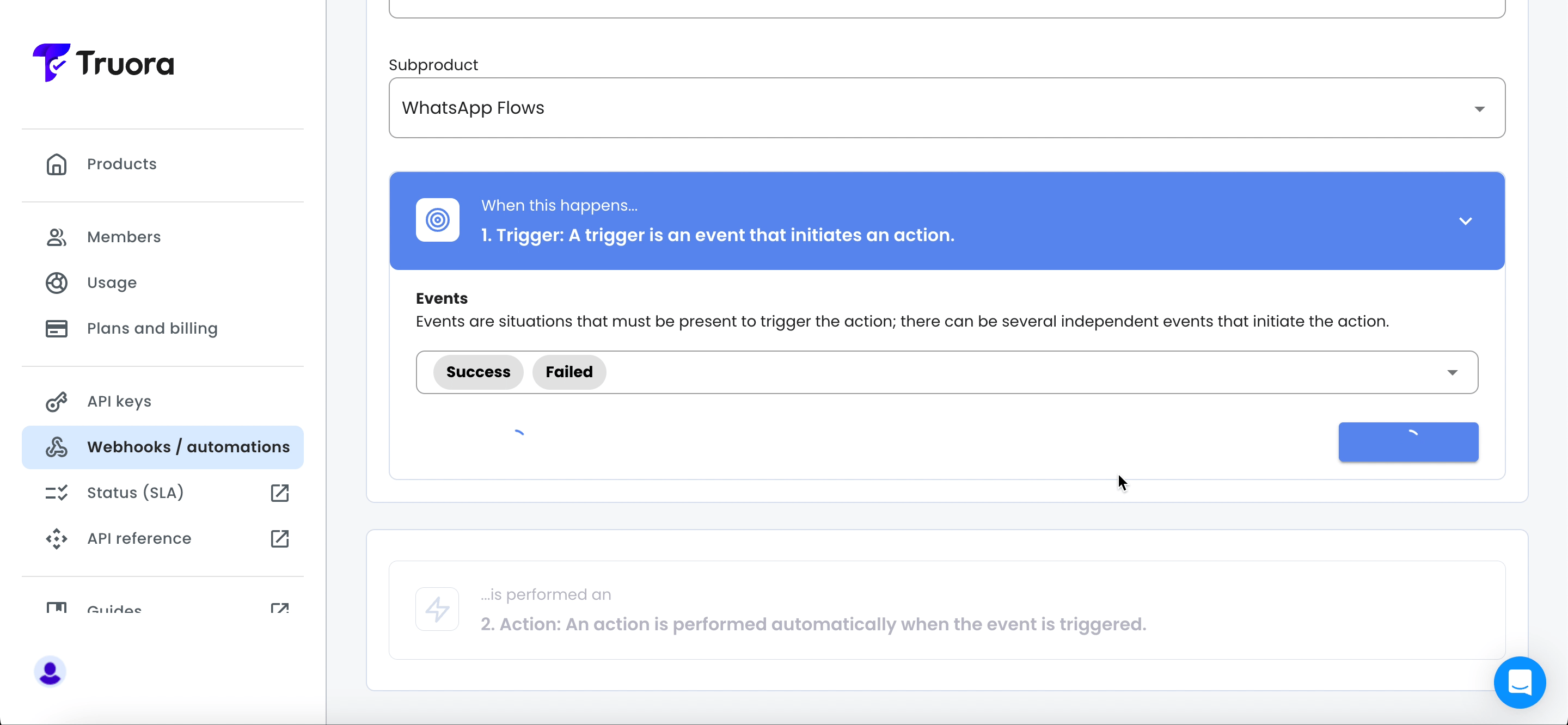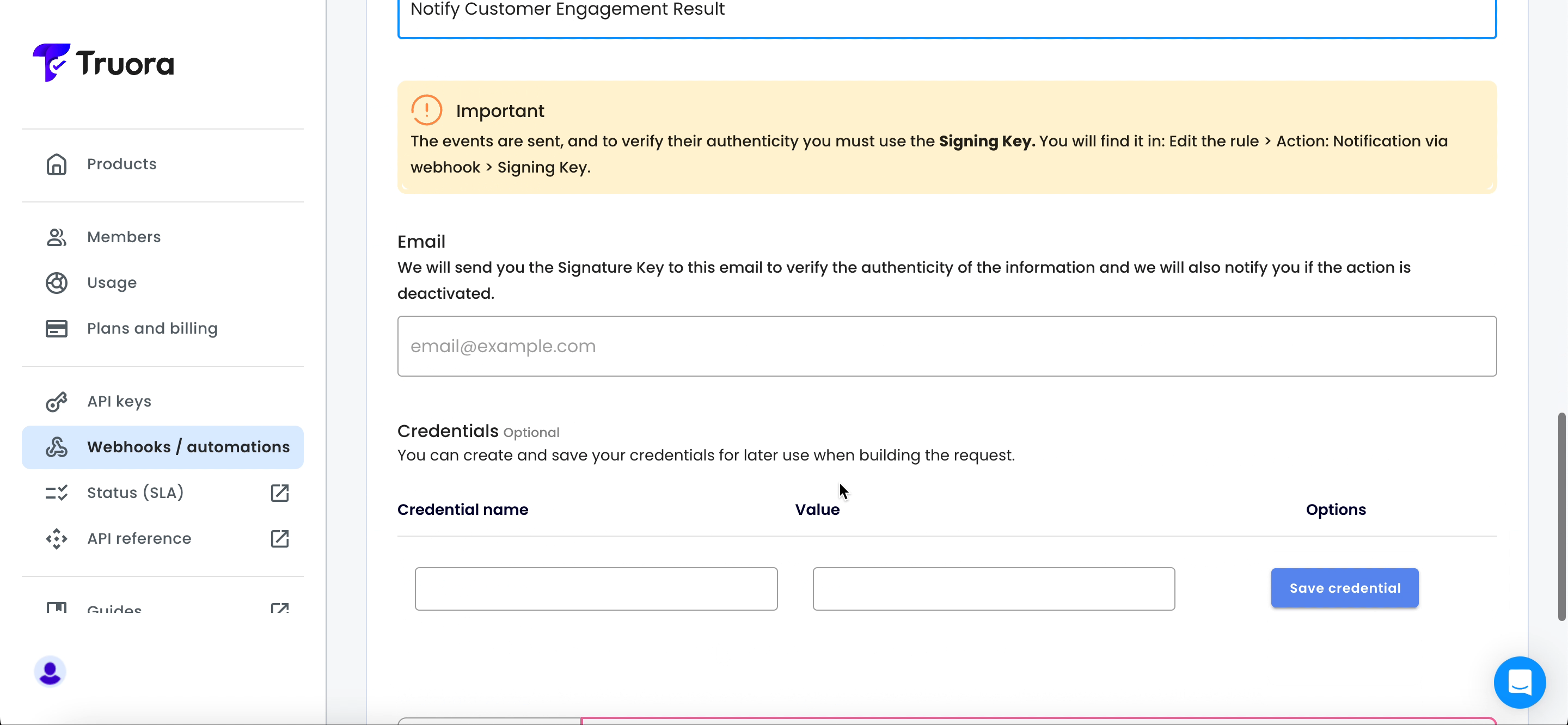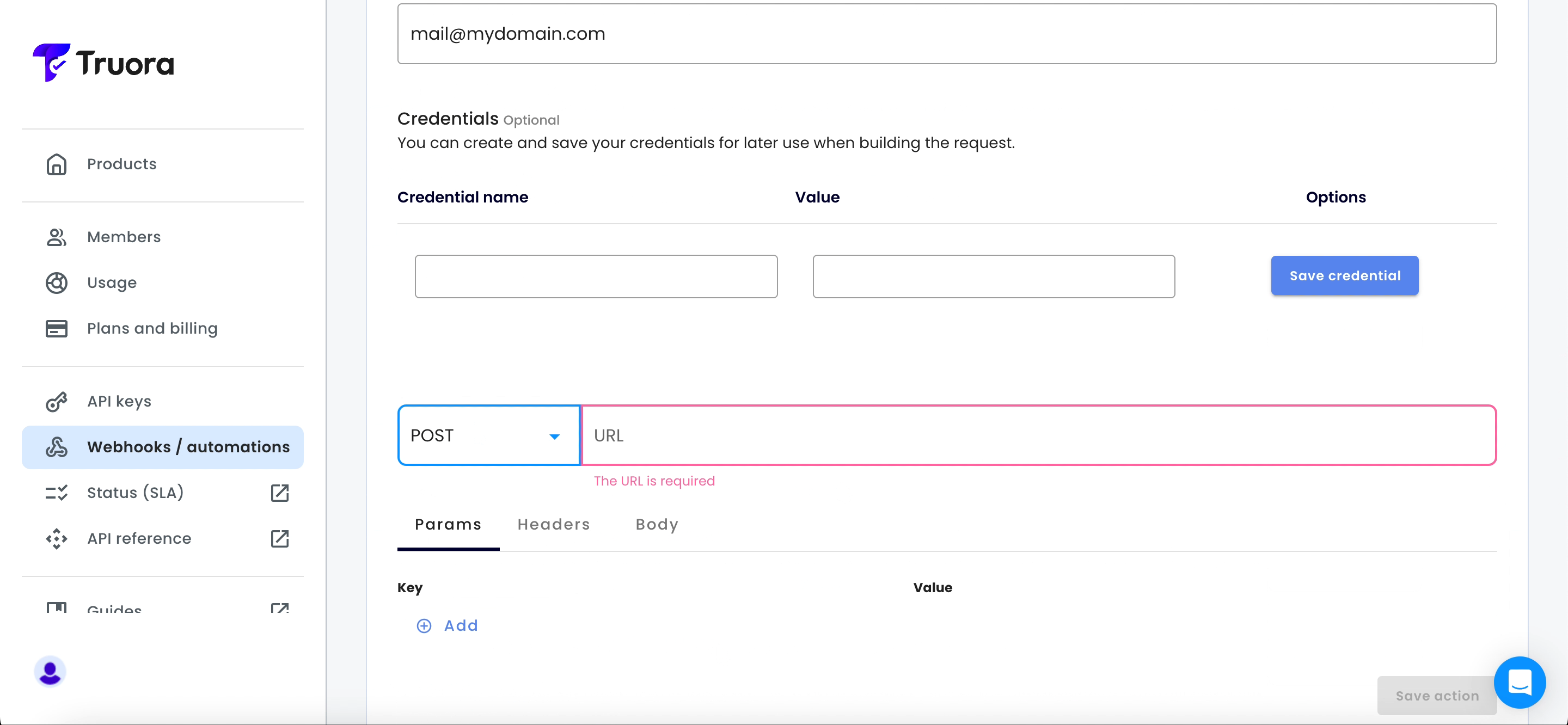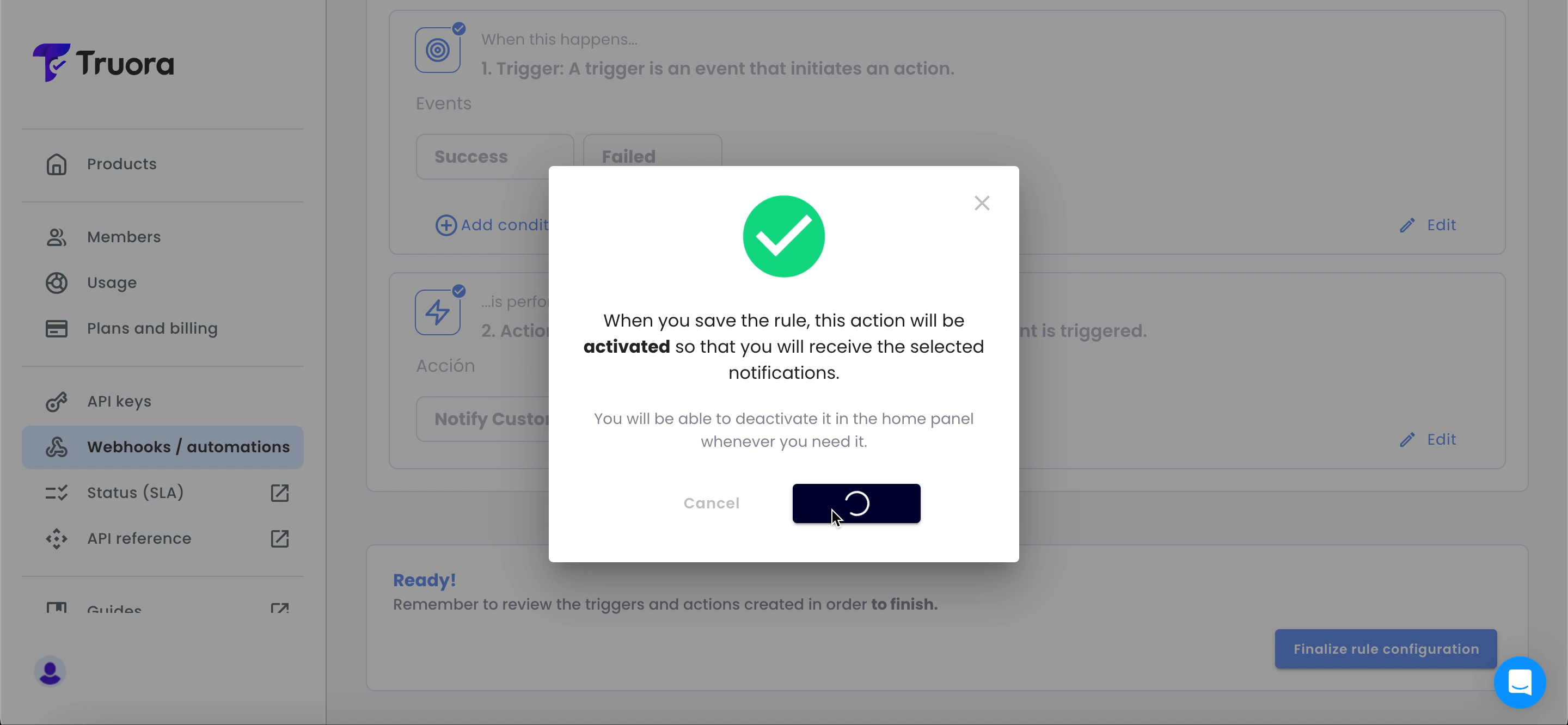
- Under Product, choose Customer Engagement and under subproduct, select WhatsApp Flows.
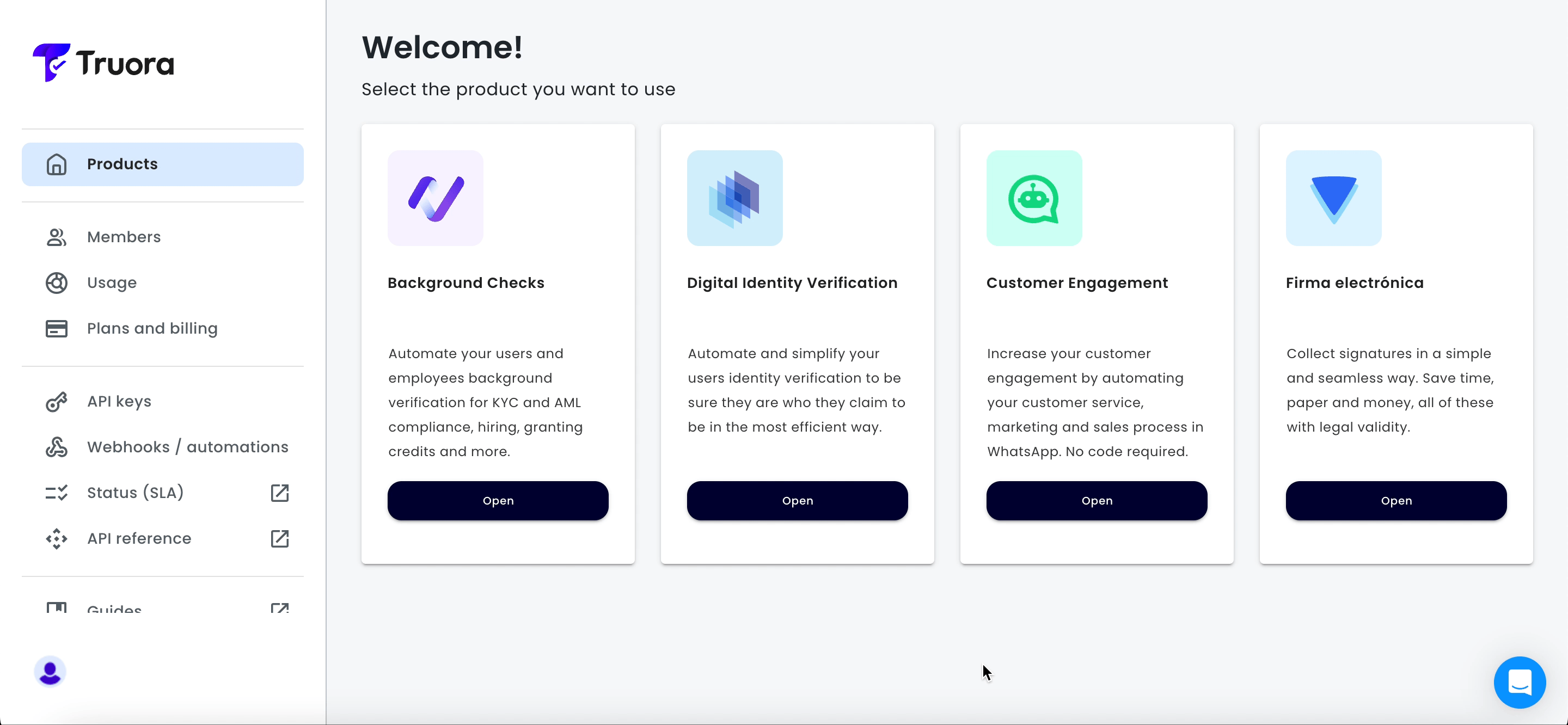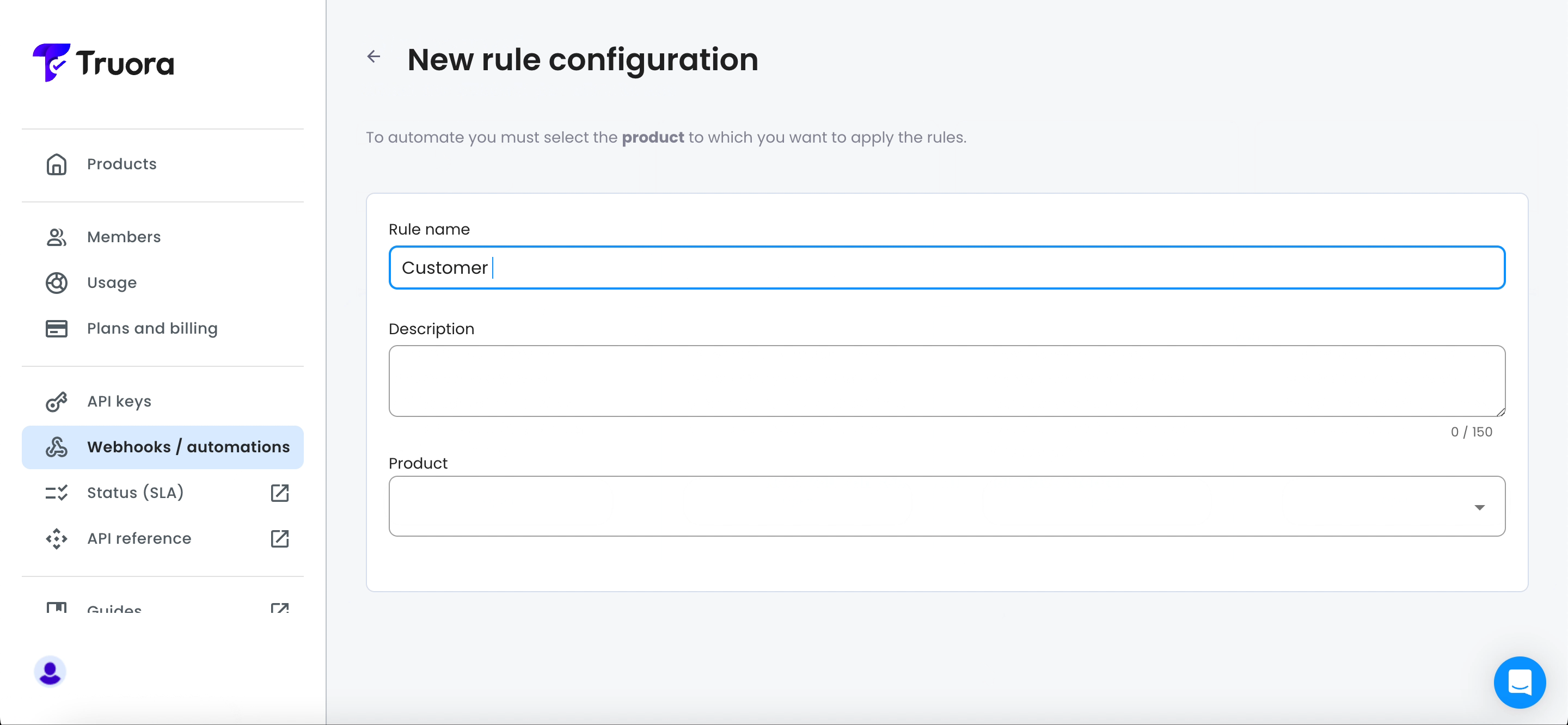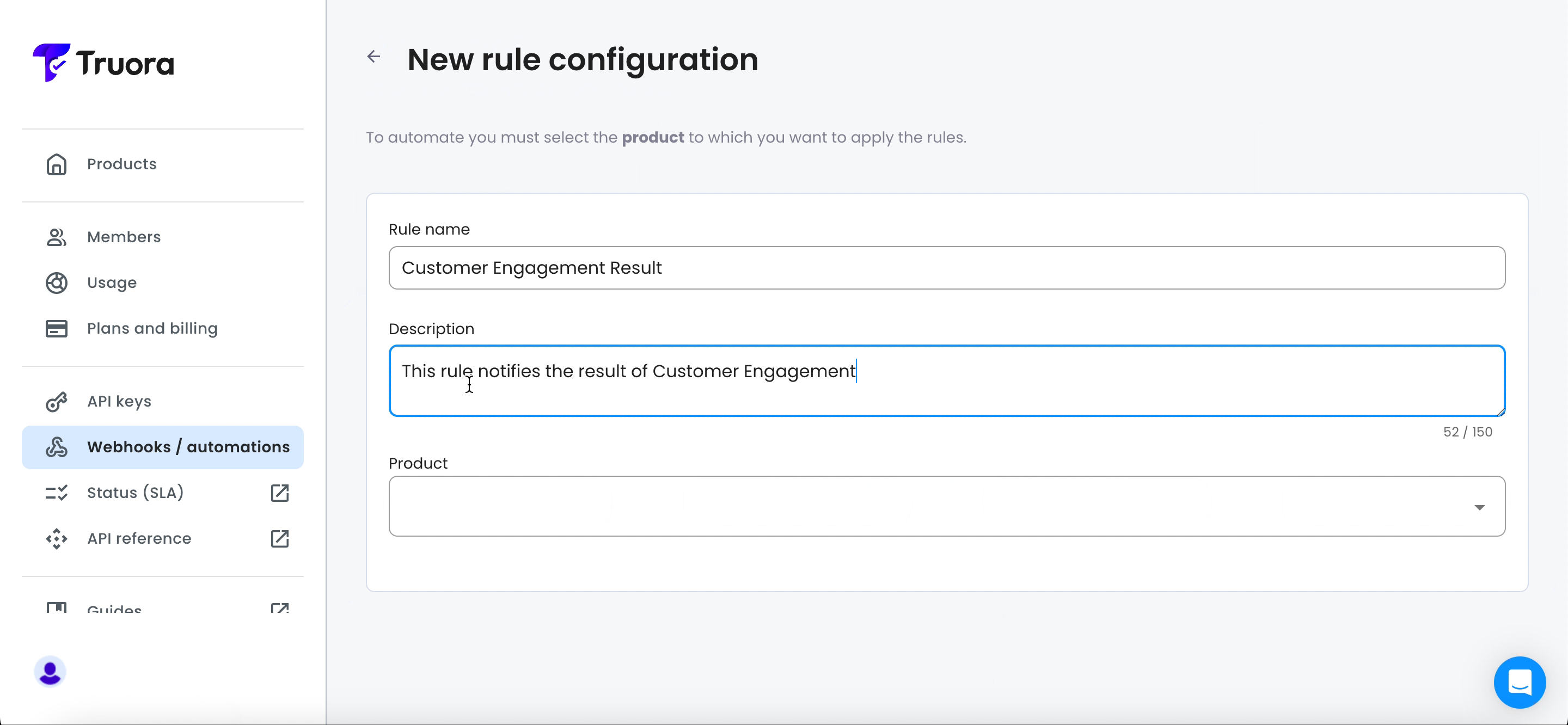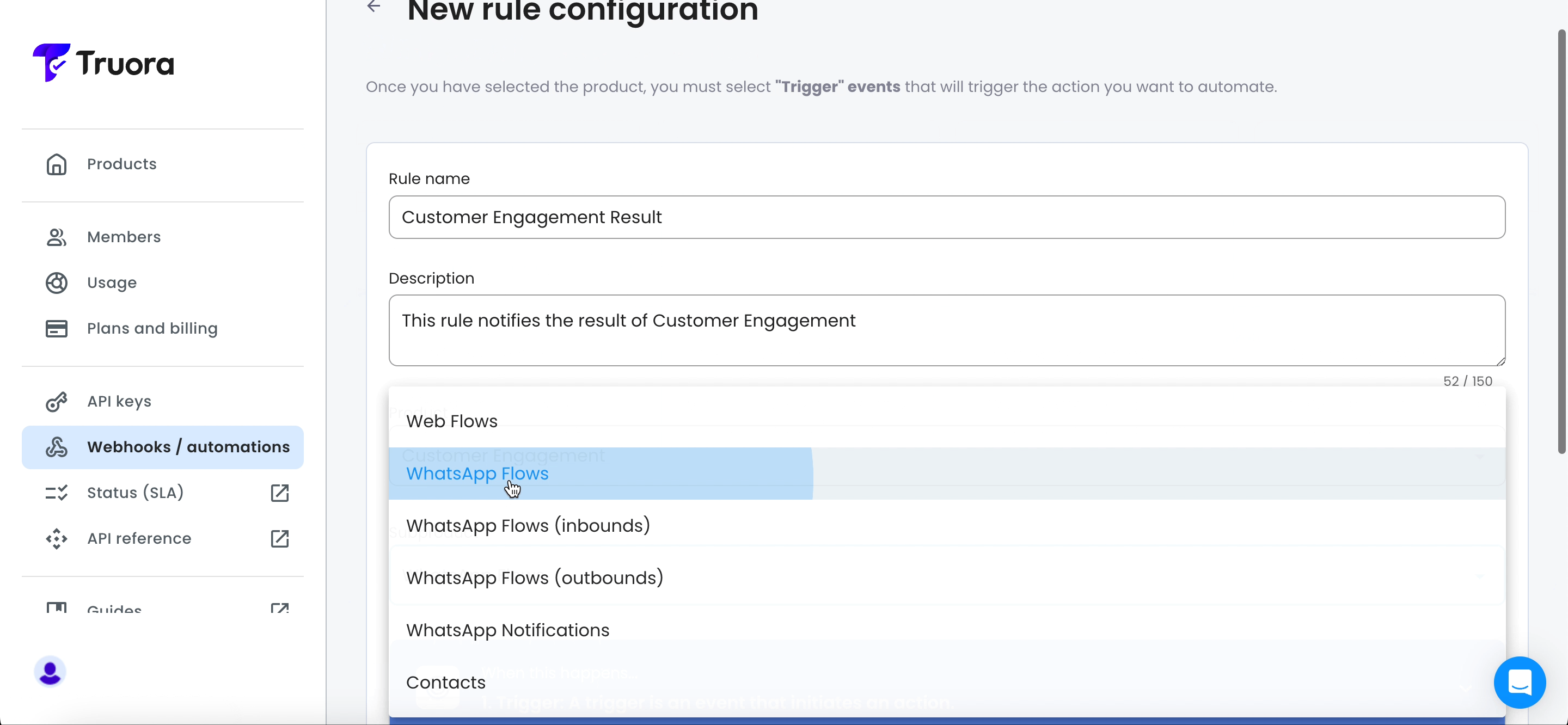
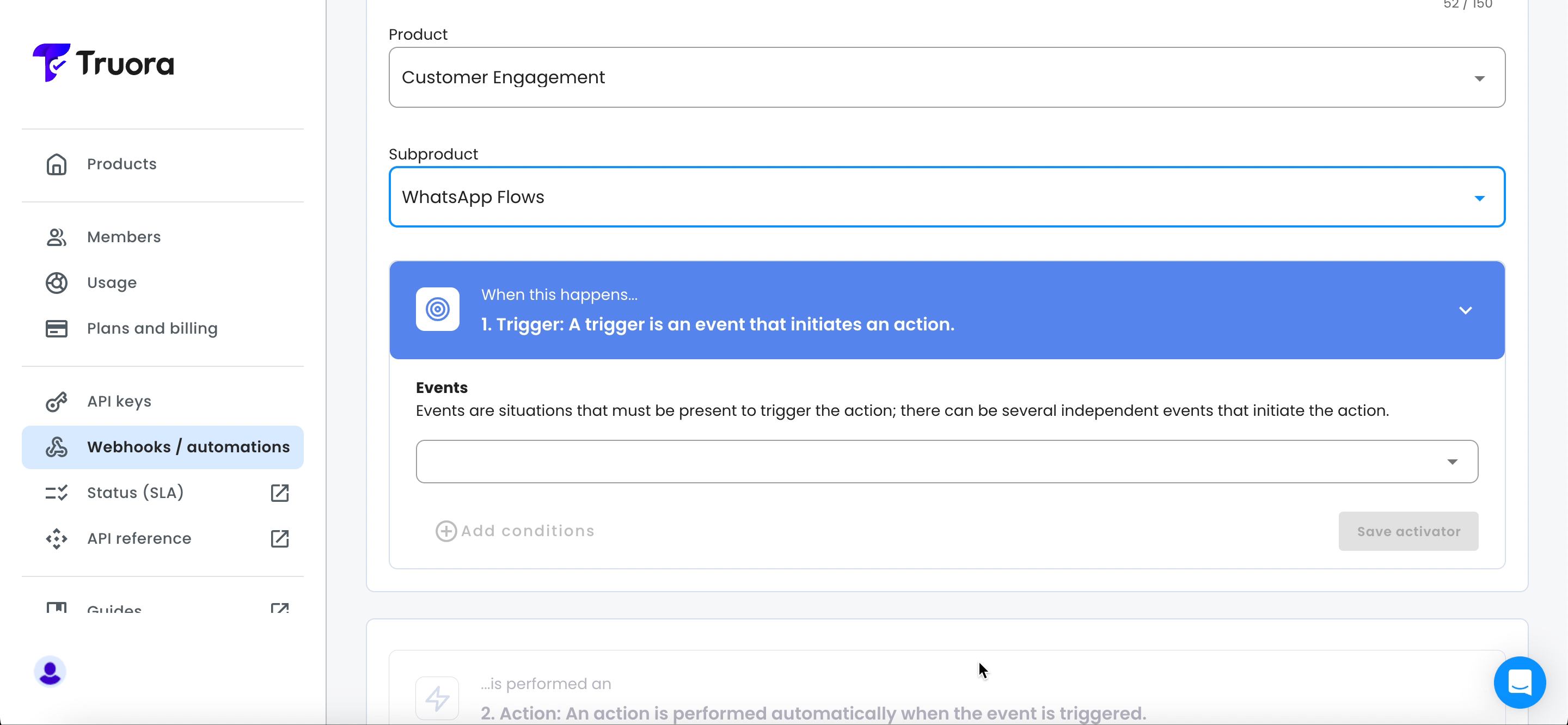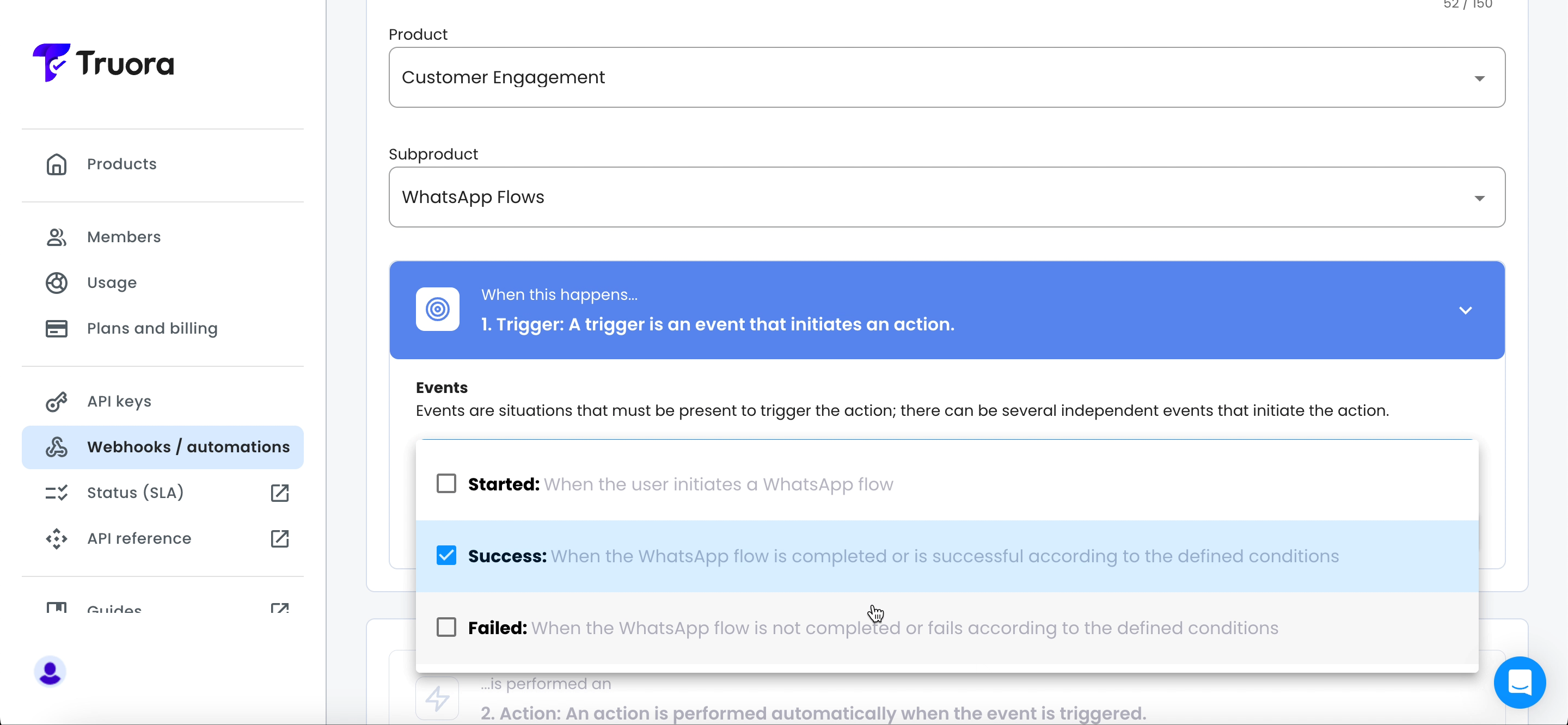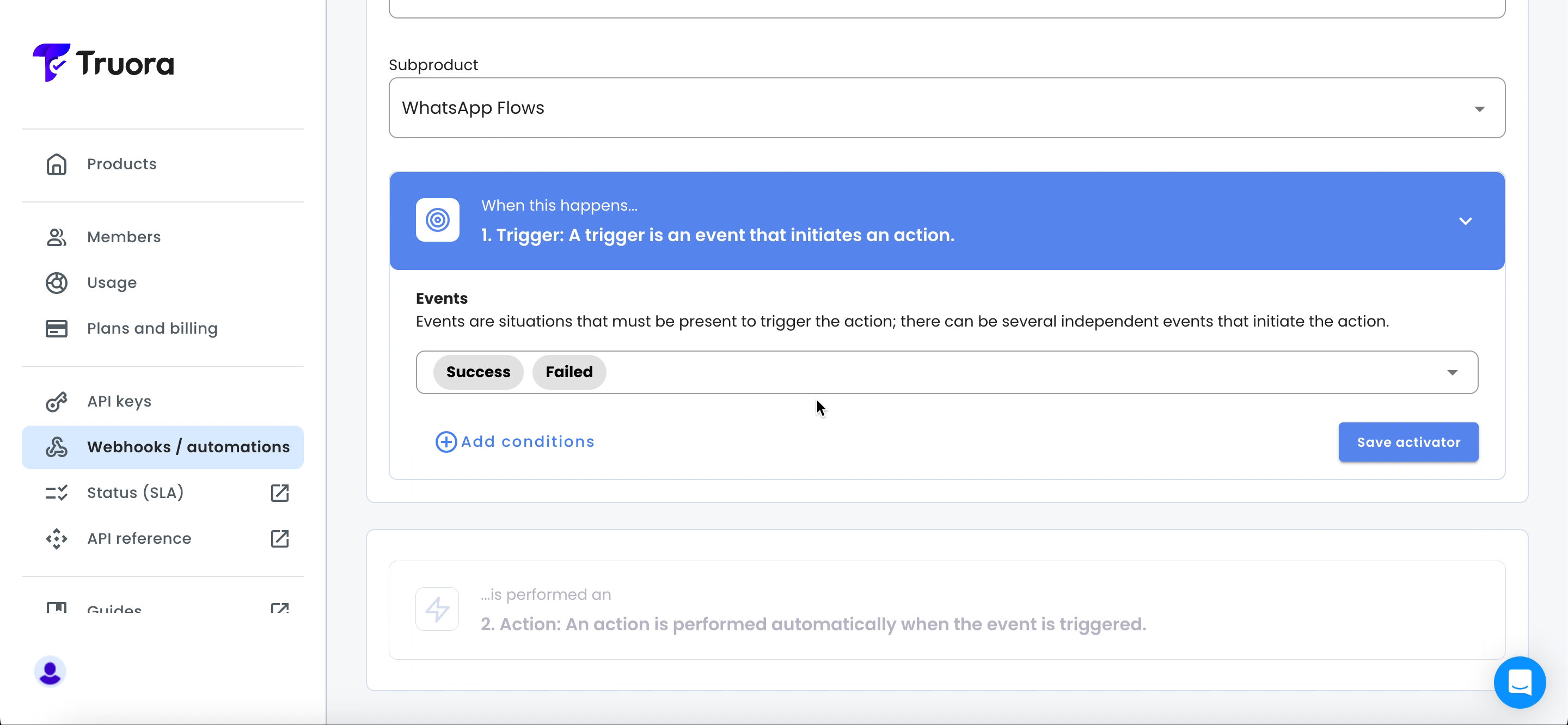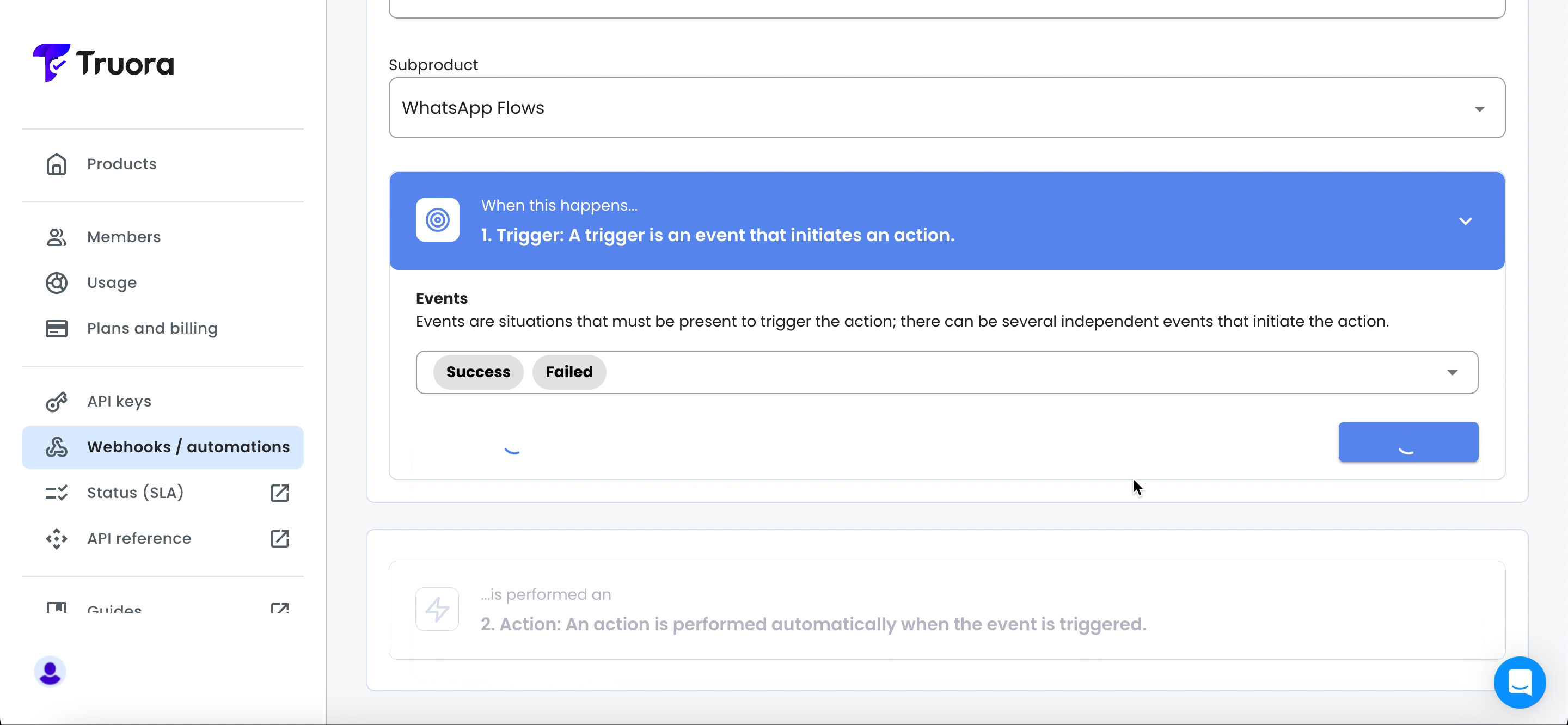
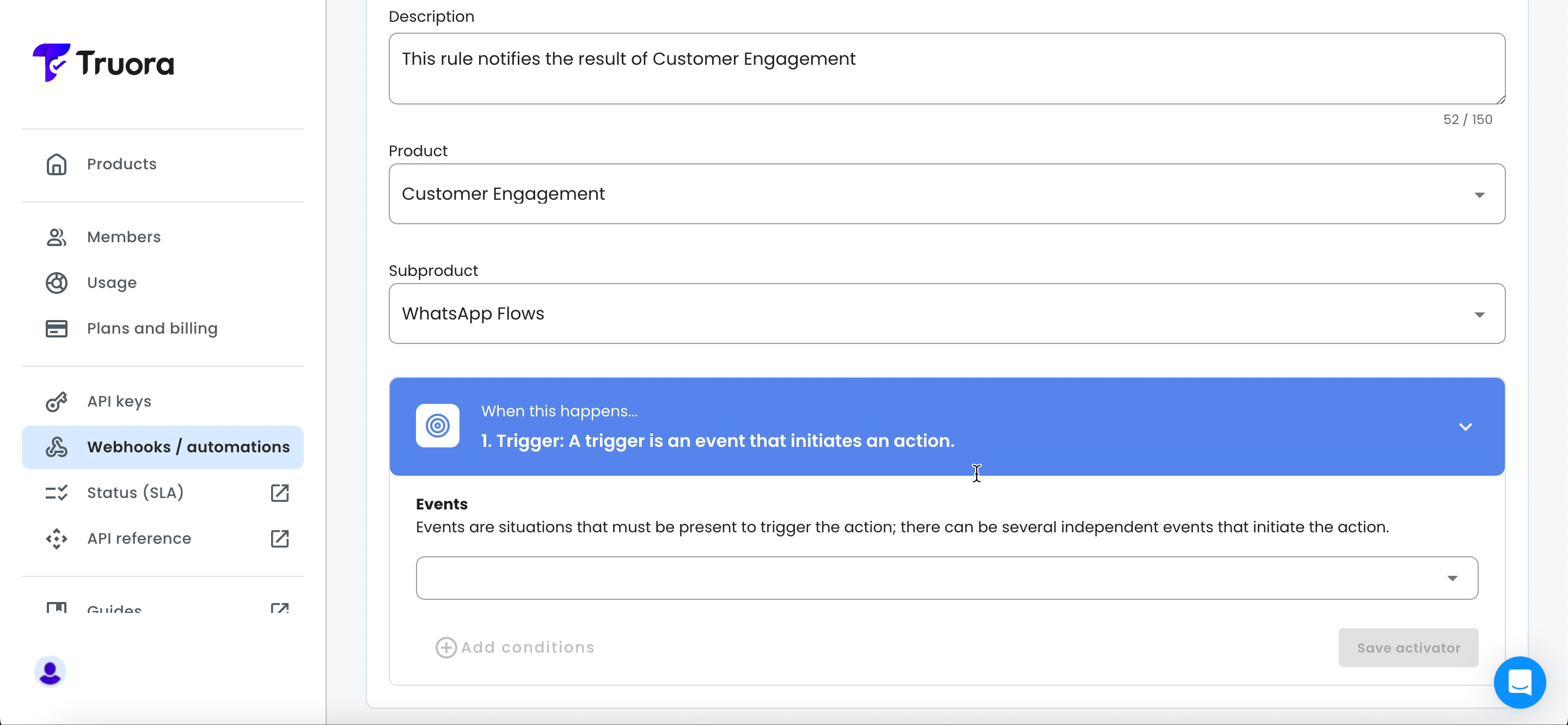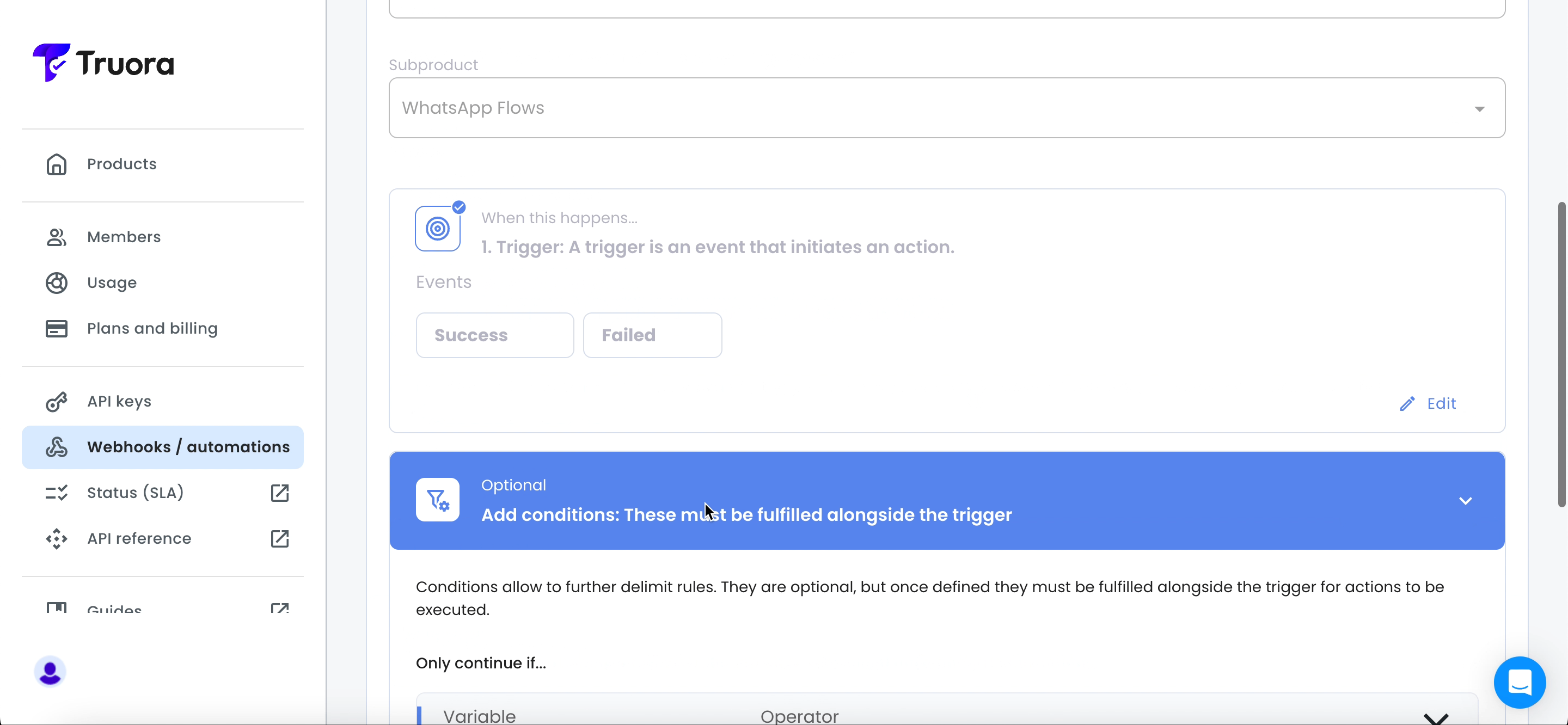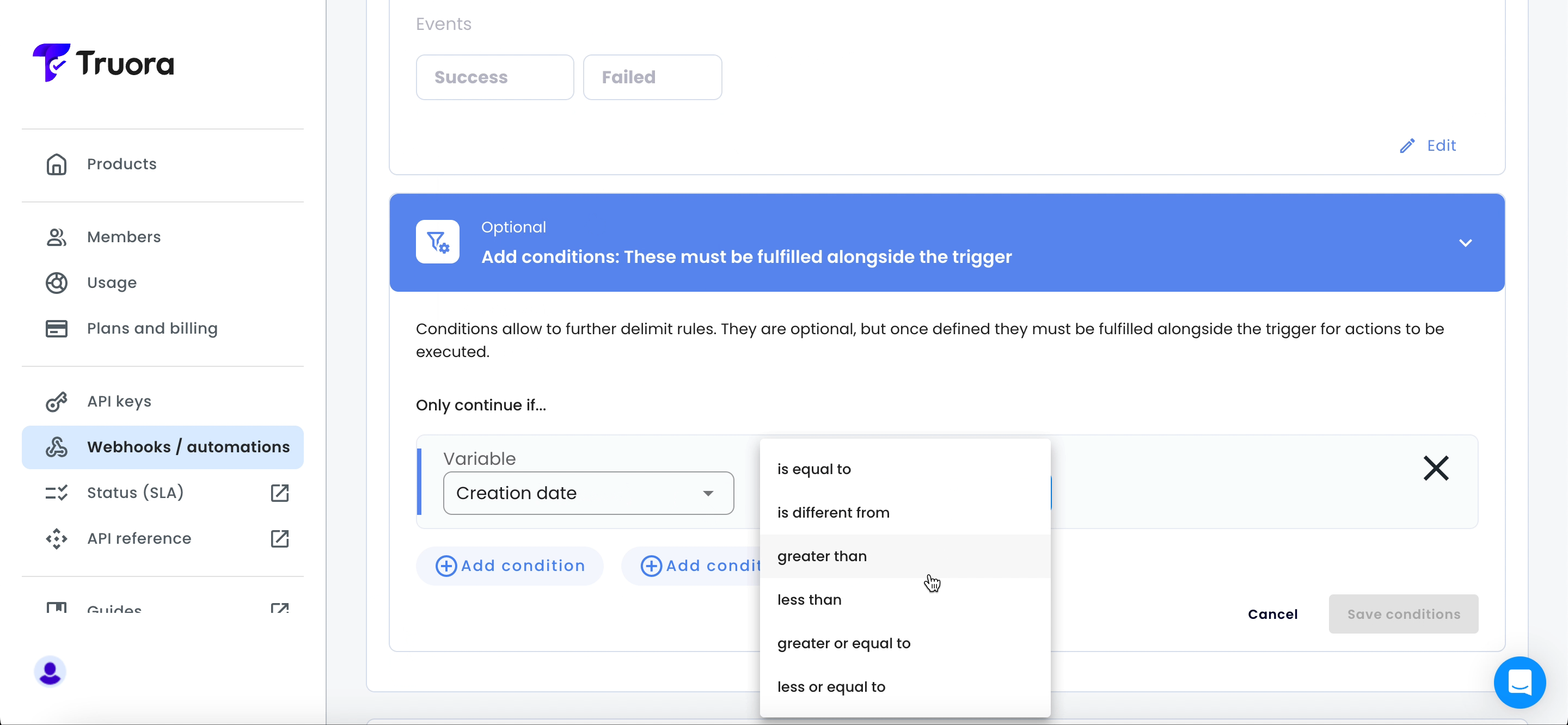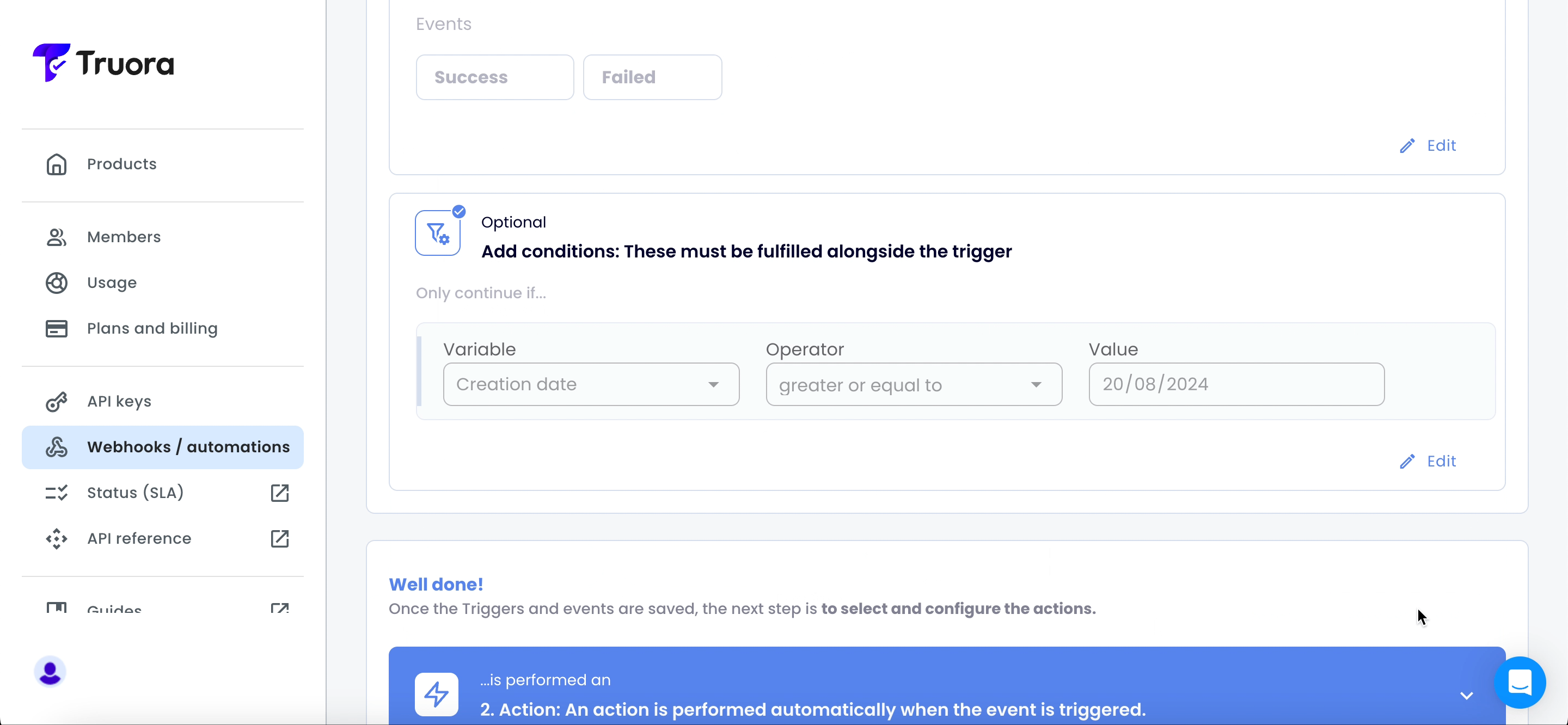
- The WhatsApp Flows sub product includes the following three events. You can select multiple events if needed, as different events might trigger the same actions based on your specific use case:
- Started: Triggered when the user initiates a WhatsApp flow.
- Success: Triggered when the WhatsApp flow is completed or successful according to the defined conditions.
- Failed: Triggered when the WhatsApp flow is not completed or fails according to the defined conditions.
- Select the events from the list and click Save activator.
- Optional: Based on the events and variables (
List of events and their variables) you can define additional conditions that must be met alongside the trigger. To add conditions, click +Add conditions.
- Scroll down to the Action section and select Notification via webhook.
- Configure the Notification via webhook action:
- Assign an identifier name.
- Provide an email to receive Webhook status updates or changes.
- Optional: If the endpoint for receiving Webhook notifications requires credentials, ensure they are added.
- Select the HTTP method and enter the URL for the Webhook.
- Optional: Add any required parameters or headers.
Note: The webhook will send its response payload in JWT format to the specified endpoint. A brief explanation of JWTs is provided later in this guide.
- Finally, save the action and save the rule:
- Click Save action.
- If no additional actions are needed, click Save actions.
- Lastly, click Finalize rule configuration to add the rule to your list of configured rules.
You are all set!
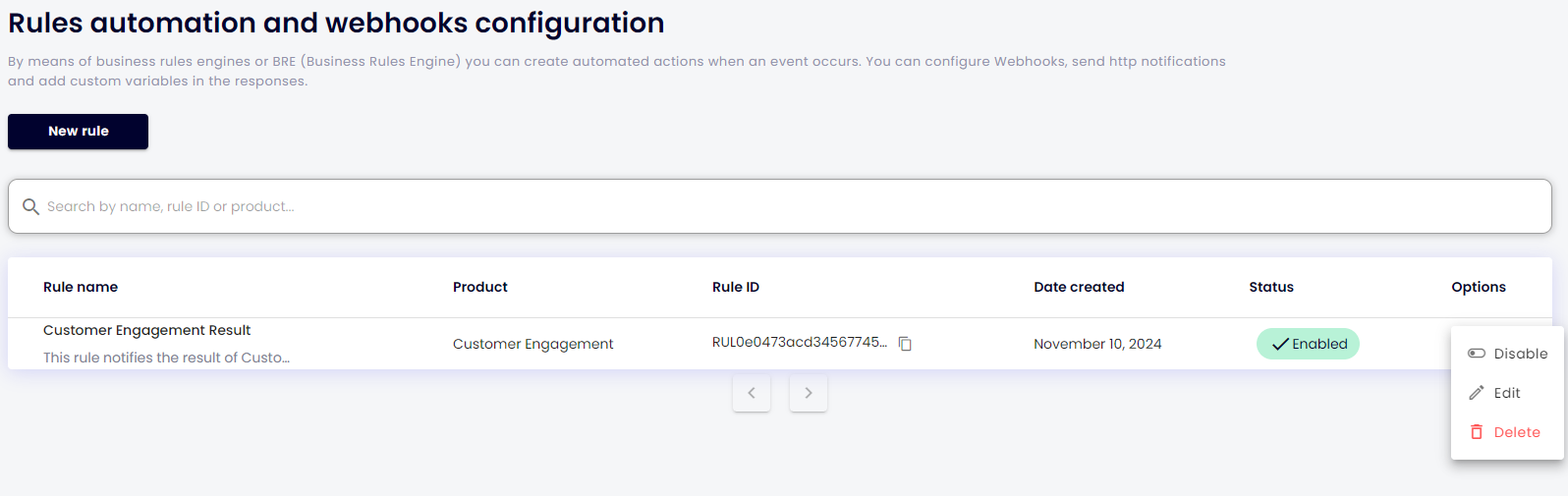
Your rule has been created successfully! You can now view its name, ID, status, and creation date in your list of rules. To edit, disable, or delete the rule, click the three dots button on the right. Feel free to explore, create additional rules, and check out the other events we support!
What is a JWT?
A JSON Web Token (JWT) is a Base64-encoded string used for authentication and the secure transfer of information between two parties. A JWT consists of three parts separated by periods (.), formatted as «header».«body».«signature».
Example:
| eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.83a9Oh1v7AAKfEr4BXxZC44gNiOb_OJ7PI3mEO4rwXE |
- Header: Contains the type of token and the encryption algorithm used.
- Payload: Includes the information to be transmitted, usually in JSON format.
- Signature: Ensures the integrity of the token, allowing verification that the JWT was issued by the legitimate source and has not been tampered with.
How to Decode a JWT?
There are several libraries available in different programming languages that allow you to decode and verify a JWT. Some of the most popular include jsonwebtoken for JavaScript, jwt-simple for Python, and jjwt for Java, among others.
In this guide, an example will be provided using the jsonwebtoken library in JavaScript.
To decode and verify a JWT, you can use the jwt.verify(…) function from jsonwebtoken. This function takes the token as the first argument and the secret key used to generate the signature as the second argument. If the signature and algorithm match, the token is valid; otherwise, it will be considered tampered with.
